The chance of future earnings or outcomes deviating from expectations is referred to as risk. Risk refers to the level of risk that an investor is ready to accept in order to profit from an investment. Risks come in a variety of forms and originate in a variety of settings. Risk management is the process of identifying, assessing, and controlling hazards to an organization’s capital and profitability. The process of creating and implementing decisions that decrease the negative impact of risk on an organization is known as risk management. It’s the process of determining the likelihood of loss or injury and then taking steps to mitigate the risk. When a person assesses the likelihood of incurring large vet expenses and determines whether or not to acquire pet insurance, this is an example of risk management. Risk classification is the technique of categorizing people based on the risks they pose, such as similarities in the costs of potential losses or damages, the frequency with which the risks arise, and whether or not efforts are done to mitigate or eliminate the risks.
Risk is divided into two types: systematic and unsystematic. Systematic Risk – The market’s total impact. Unsystematic Risk — Uncertainty about a specific asset or firm. Political/Regulatory Risk – The consequences of political actions and regulatory changes. Financial risks can be categorized in a number of ways. One technique for doing so is to divide financial risk into four categories: market risk, credit risk, liquidity risk, and operational risk. A risk categorization system serves three basic purposes: to protect the financial health of the insurance programme, to improve fairness, and to allow economic incentives to work, resulting in widespread coverage availability. It’s also known as “risk retention,” and it’s a type of risk management that’s widespread in business and finance.
Loss prevention and control are two methods for lowering risk. Medical care, fire departments, night security guards, sprinkler systems, and burglar alarms are examples of risk reduction—attempts to deal with risk by preventing loss or reducing the possibility that it will occur. Risk transfer is a typical risk management approach in which an individual or entity’s potential loss from an adverse outcome is shifted to a third party.
To compensate the third party for taking on the risk, the individual or corporation will usually make monthly payments to the third party. Any condition, event, occurrence, or situation that has the potential to have a positive influence on a project or business is referred to as a positive risk. Taking a risk does not have to be a bad thing; there are advantages to taking a risk. It has the potential to help your project achieve its objectives. By developing a risk management plan and taking precautionary efforts, an organization can save money and preserve its future. Risk management provides the following benefits as well: Ensures a safe and secure working environment for all workers and customers.
A risk management plan is a method for recognizing, assessing, and managing risk that is structured and consistent. It has a method for updating and revising the evaluation on a regular basis in light of new events or actions made. In general, risks with a high likelihood of producing financial loss or damage should be avoided. IT security threats and data-related hazards, as well as risk management measures to mitigate them, have risen to the top of the priority list for digital businesses. As a result, risk management plans increasingly include ways for identifying and controlling threats to digital assets such as sensitive company data, a customer’s personally identifiable information (PII), and intellectual property.
Risk Management Strategy for Business
Every company and organization is vulnerable to unforeseeable, destructive events that could cost them money or compel them to close forever. Risk management enables businesses to prepare for the unforeseeable by reducing risks and expenses before they occur.
A company can save money and secure its future by developing a risk management plan and considering the many potential hazards or events before they occur. This is because a robust risk management plan may help a company set procedures to avoid potential threats, lessen their impact if they do materialize, and deal with the consequences of those threats.
Organizations that effectively recognize and manage risk can be more confident in their business decisions.
Risk management also has the following major advantages:
- It creates a safe and secure work environment for all employees and consumers.
- Increases the stability of business operations while minimizing legal liability.
- Provides protection against incidents that are harmful to the firm as well as the environment.
- Ensures that all individuals and assets involved are safe from harm.
- Assists in determining the insurance needs of the organization in order to prevent paying unnecessary premiums.
It was also stressed the significance of combining risk management with patient safety. In hospitals and enterprises, risk management and patient safety divisions are normally segregated; they have different leadership, goals, and scope. Some hospitals, on the other hand, are realizing that the ability to offer safe, high-quality patient care is critical to the protection of financial assets and, as a result, should be included in risk management.
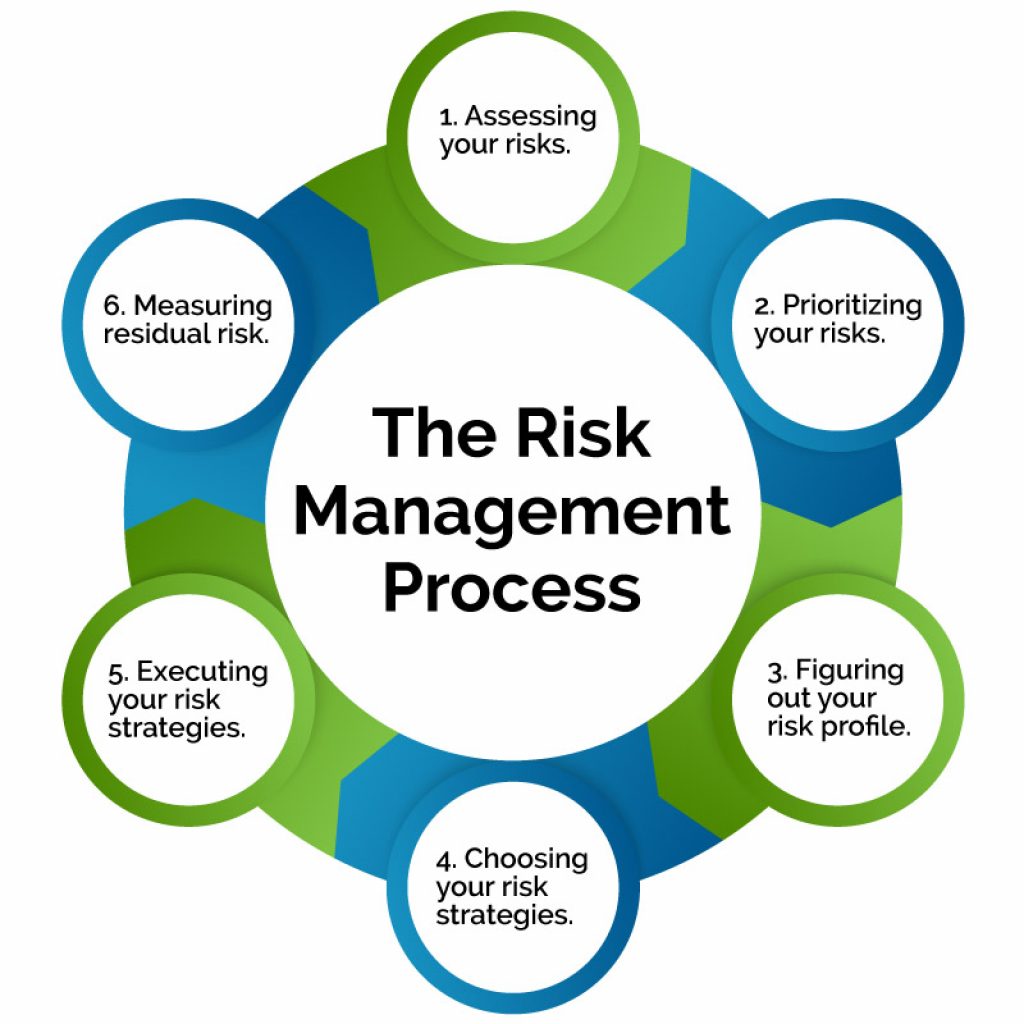
Risk Management Strategies and Processes
All risk management plans follow the same steps that combine to make up the overall risk management process:
- Create a Context: Recognize the circumstances under which the remainder of the procedure will occur. The criteria for assessing risk, as well as the structure for the analysis, should be specified.
- Identifying Potential Risks: The business analyses and specifies potential risks that could have a negative impact on a certain process or project.
- Risk Assessment: The organization evaluates the possibility of particular categories of the risk occurring, as well as the potential consequences, after recognizing them.
- Identifying and Assessing Risks: The risk is further investigated after assessing its overall likelihood of occurrence as well as its overall impact. The corporation can then decide whether the risk is acceptable and whether it is willing to take it on based on its risk appetite.
- Risk Reduction: Companies analyze their highest-ranking risks during this step and design a plan to mitigate them using specific risk controls. In the event that the risk materializes, these procedures include risk mitigation approaches, risk preventive tactics, and contingency preparations.
- Keep an Eye on the Risks: Part of the mitigation plan is to follow up on both the risks and the broader strategy to continuously monitor and track new and existing hazards. The overall risk management approach should also be examined and adjusted as necessary.
- Communicate and Consult: Internal and external stakeholders should be communicated with at each relevant phase of the risk management process, as well as through the entire process.
Risk management strategies should also attempt to answer the following questions:
- What could possibly go wrong? Take into account both the overall workplace and individual tasks.
- What impact will it have on the organization? Consider the event’s likelihood and if it will have a significant or minor impact.
- Is there anything that can be done? What safety measures may be taken to avoid the loss? What steps should be taken to recover if a loss occurs?
- What will the organization do if something goes wrong?
Approaches to Risk Management:
After the company’s distinct risks are identified and the risk management process has been applied, there are several different strategies companies can take in regard to different types of risk:
- Risk Avoidance: While it is difficult to be able to completely avoid all risks, a risk-avoidance strategy aids to deflect as many risks as possible in order to avoid the costly and disruptive repercussions of a catastrophe.
- Risk Reduction: Certain dangers can sometimes be reduced in the amount of damage they bring to a company’s operations.
- Risk Sharing: The indication of risk is sometimes shared or spread among a number of project participants or corporate units.
- Risk Retaining: Occasionally, businesses conclude that a risk is worthwhile from a business sense, and they choose to keep the risk and deal with the consequences. Companies will generally keep a certain amount of risk if the expected return on a project is greater than the costs of its potential risk.
Limitations:
While risk management may be a very beneficial technique for businesses, it does have some drawbacks that should be considered. Many risk analysis procedures, such as developing a model or running a simulation, necessitate the collection of vast volumes of data. This vast data collection can be costly, and its accuracy cannot be guaranteed.
Furthermore, if simplistic indicators are used to reflect the much more complicated facts of the issue, the use of data in decision-making processes may have bad results. Similarly, extending a decision made for one minor element of the project to the entire project can result in unforeseen outcomes.
Another constraint is a lack of competence in the analysis as well as time. To simulate occurrences that could have a detrimental influence on the organization, computer software programs have been developed. These complicated algorithms, while cost-effective, necessitate skilled employees with a broad range of skills and expertise in order to appropriately interpret the generated findings. Highly trained professionals are also required to analyze previous data in order to identify dangers. It’s possible that these people won’t always be assigned to the project. Even if they are, there is sometimes insufficient time to collect all of their findings, resulting in disagreements.
Other Limitations Include:
- An erroneous sense of security. Value-at-risk measurements are concerned with the past rather than the future. As a result, the better the situation appears the longer things run well. Unfortunately, this increases the likelihood of a slump.
- The phantom of control. Risk models can give businesses the misleading impression that they can assess and control all possible risks. This could lead to a company overlooking the prospect of new or unforeseen threats. Furthermore, because new products have no past data, there is no experience on which to build models.
- Risk management is immature, making it impossible to perceive and understand the full picture of cumulative risk.
Risks Your Coworking Business Should Address :
As the popularity of shared office spaces grows, so does the number of people who are interested in learning more about the hazards that come with owning one. This is unsurprising, given everything, including enterprises and investments, comes with its own set of risks – and serviced office spaces are no exception. On that topic, let’s take a look at five hazards that present and aspiring business owners should be aware of in order to maintain a fully furnished office space that thrives.
Data Privacy and Cybersecurity:
Working in an open space with dozens of other businesses and sharing WiFi is a data disaster waiting to happen. Given that a coworking space’s WiFi connection is one of the most significant services it provides, it makes sense to appreciate and safeguard the security of not only your own company’s data but also that of your clients’. After all, your customers want to know that their personal information won’t fall into the hands of competitors or cybercriminals attempting to break into your network. A data breach might not only harm a coworking space’s brand but can also result in a liability case.
Marcus’ guide to cyber security basics advocates keeping all computer operating systems and other equipment up to date, as well as creating strong WiFi passwords that are changed every few days, to help mitigate the problem. Put in place certain security processes in the event of a breach, and aim to raise cyber security awareness among your clientele. While there are only so many steps you can take to ensure your clients’ security, knowing the basics and performing the little things can go a long way.
Theft of Equipment:
Recognize that you can’t control what your clients do, but you can do your best to keep unpleasant activities like theft from occurring in your coworking space. The danger of theft at a coworking space is higher than in a regular office because there are many different sorts of businesses working there and a steady stream of individuals coming in and out. While the type of theft depends on the packages or memberships they buy, it’s still a good idea to make sure all of your clients’ valuables are safe. For example, provide safe lockers for clients to store their belongings, and install cameras throughout the area to monitor every perspective.
Access Management:
What software do you use to control who has access to your coworking space? Mobile devices, key fobs, or key cards? Because former clients who still have access to your place can constitute a significant risk, it’s critical to address how you grant and remove access to your area. These clients have the ability to enter without being noticed, or even steal equipment from present clients. It is, therefore, critical to provide and revoke access at the appropriate moments. We propose syncing your coworking space software with your access system so that access may be granted and canceled at any moment for new and previous clients. If you use key cards or key fobs, it’s also a good idea to have a procedure or protocol in place for when new or returning renters arrive at the coworking space.
